Overview
Many organisations have embarked on a program of work to move their IT systems and services to the cloud. Their cloud services are normally a mix of M365, Azure, Entra, AWS, SaaS services and on-premises systems. Where a system is cloud-ready they are lifted and shifted to a cloud environment. Where the system is not suitable to migrate to the cloud, they are being redeveloped into a cloud native solution or kept on-premises until they are replaced at end of life. This has presented challenges in how request-based access management is managed across an expanding application landscape.
Apporetum is a commercial of-the shelf Enterprise grade IGA solution that has been designed to address this problem while ensuring cyber security and operational risk associated with the continued expansion of cloud applications, SaaS services and on-premises systems is addressed.
Apporetum provides:
- Business intimacy for access management and identity management governance
- Delegated access management for applications & resources across multi-tenant, multi cloud and on-premises systems.
- Single view of enterprise access for all integrated application in a single console.
- Ability to detect unsanctioned access
- Ability to suspend/unsuspend access based on user, role, application or trusted partner. The access can be restored when required.
- Identity management across a multi-tenant and hybrid environment.
- All identity data is kept within the organisation's tenant boundaries maintaining data sovereignty and jurisdiction
Benefits
Apporetum provide a business intimacy layer to:
- Centralise access management for an application landscape across multiple cloud tenants, on-premises directories and legacy systems that are not directory attached.
- Provide an enterprise ‘plane’ to govern and control users and the role, application or trusted partner (supply chain) access to resources.
- Modernise access control for cloud applications – moving away from help desk requests to self-service with integration to service management tools.
- Modernise identity management for the business – moving away from help desk requests to self-service with integration to service management tools and automation.
- Reduce cyber security and operational risks introduced by an increasingly complex application landscape providing ability to easily detect unsanctioned access and leveraging lifecycle management of users.
- Integrate with Entra ID and modern authentication protocols.
- Shift away from access management being tightly coupled to a unintelligible group name, to business focused applications leveraging enterprise capabilities.
- Access reviews in real time without the cumbersome use of spreadsheets.
Architecture
Apporetum is a native Azure app integrated with Entra ID, Microsoft Graph, Microsoft M365 services and on-premises systems such as Active Directory or CSV feeds from bespoke systems. It is presented as a application hosted entirely within a secured enclave in the customer's tenant with managed JIT access to the a managed application deployed from the Microsoft Marketplace. It preserves the organisation’s data privacy, jurisdiction, sovereignty, and security posture. This architecture means that there is no need to export data to the wider internet or punch holes through you network firewalls so that SaaS IGA applications can access the identities in your tenant.
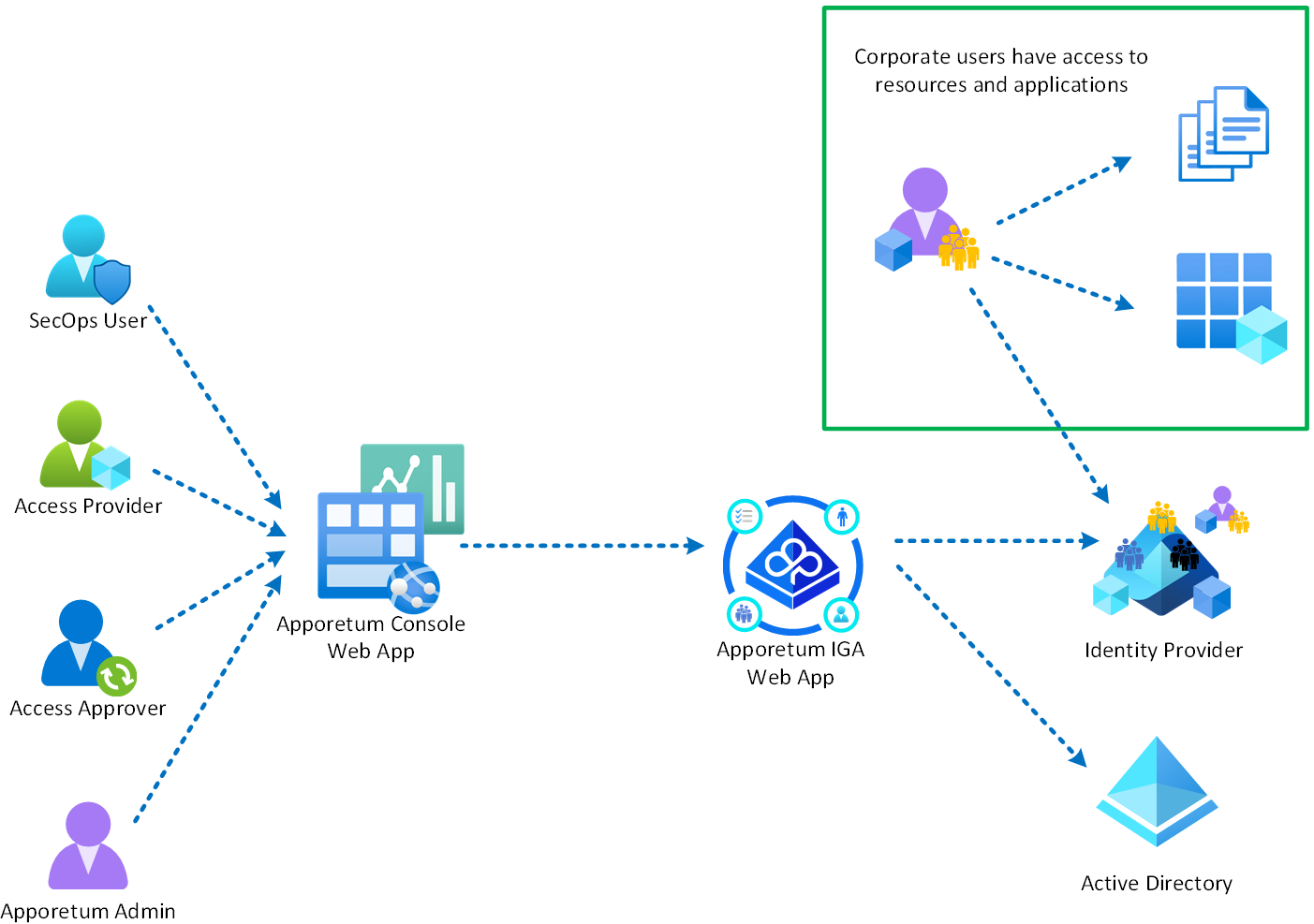
Personas
The system is designed for the following personas that will be able to perform the following self-service functions:
| Role | Description |
|---|---|
| Access Provider | Is a business user that can grant access to applications and resources that they have permission to manage. |
| Access Approver | Is a business user that is required to approve access requests to applications and resources that they have been assigned to manage. |
| Application Owner | Is a business user that is required to manage the Owners, Approvers and Providers to the applications they have been assigned to manage. |
| SecOps User | SecOps users have access to view all activity within the system and suspend user access or suspend all access to a resource. |
| Corporate User | Corporate users can access the resources they require to perform their duties. |
| System Admin | Is a position of trust that can change system wide settings and add application and role configurations to the system. |
User Roles and Responsibilities
The user types within the Apporetum Service are described below. The entitlements policy will vary based on the user type:
- Application Owner: An application is assigned a business owner as the contact point for any queries relating to access to an application. They currently do not perform any management tasks within Apporetum but can view access reports for their applications. They are the contact for the Apporetum Admins to contact regarding who are to be allocated to the Access Approver and Access Provider roles.
- Access Provider: This user role is allocated to a business user who will add and remove access user to the roles in the application they manage. They have access only to the role management of applications of they have been allocated to by the Apporetum Admin.
- Access Approver: This role allows access to the Service to perform approvals of access requests. They have no other capabilities with the system.
- SecOps User: This user type is normally allocated to members of the IT security operations team. They have access to all security events within the system and can see all access assignment to users and application roles. They also have the capability to suspend the access for a user, role or application or resource. This is a position of trust.
- System Admin: This user type is normally allocated to members of the IT operations team or IAM team. They perform the configuration of the applications within Apporetum and assignment of users to the specific application management roles. This user type will manage who receives the other Apporetum roles. This may also be automated through the identity management system. This is a position of trust.